![[Compaq]](../../images/compaq.gif)
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
| Document revision date: 28 June 1999 | |
![[Compaq]](../../images/compaq.gif) |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
|
|
| Previous | Contents |
This chapter describes the access-control list (ACL) files and their syntax. ACL files are text files that contain lists that define who can access resources stored on your web server. By default, the web server uses one ACL file that contains all of the lists for access to your server. However, you can create multiple ACL files and reference them in the obj.conf file.
You need to know the syntax and function of ACL files if you plan on customizing access control using the access-control API. For example, you might use the access control API to interface with a database, such as an Oracle or Informix database. For more information on the API, see the DevEdge site at:
http://developer.netscape.com/library/documentation/index.html |
All ACL files must follow a specific format and syntax. An ACL file is a text file containing one or more ACLs. All ACL files must begin with the version number they use. There can be only one version line and it can appear after any comment lines. For example:
version 3.01; |
You can include comments in the file by beginning the comment line with the # sign.
Each ACL in the file begins with a statement that defines its type. ACLs can follow one of three types:
The type line begins with the letters acl and then includes the type information in double-quotation marks followed by a semicolon. Each type information for all ACLs must be a unique name--even among different ACL files. The following lines are examples of several different types of ACLs:
acl "path=/usr/netscape/suitespot/docroot1/sales"; acl "*.html"; acl "default"; acl "uri=/mydocs/"; |
After you define the type of ACL, you can have one or more statements
that define the method used with the ACL (authentication statements)
and the people and computers who are allowed or denied access
(authorization statements). The following sections describe the syntax
for these statements.
6.1.1 Authentication statements
ACLs can optionally specify the authentication method the server must use when processing the ACL. There are two general methods:
By default, the server uses the Basic method for any ACL that doesn't specify a method. You can change the default setting by editing the following line in the magnus.conf file:
Init fn=acl-set-default-method method=SSL |
Each authenticate line must specify what list (users, groups or both) the server should use when authenticating users. The following authentication statement, which would appear after the ACL type line, specifies basic authentication with users matched to individual users in the database or directory:
authenticate (user) {
method = basic;
};
|
The following example uses SSL as the authentication method for users and groups:
authenticate (user, group) {
method = ssl;
};
|
Any allow or deny statements must match the lists you specify in the authenticate line. That is, if the line says authenticate (user), the allow or deny line must also specify users. The following example allows any user whose user name begins with the letters sales: |
authenticate (user)
allow (all)
user = sales*
|
If the last line was changed to group = sales, then the ACL would fail
because there are no groups in the user lists.
6.1.2 Authorization statements
Each ACL entry can include one or more authorization statements. Authorization statements specify who is allowed or denied access to a server resource. Use the following syntax when writing authorization statements:
allow | deny [absolute] (right[,right...]) attribute qualifier expression; |
Start each line with either allow or deny. It's usually a good idea to deny access to everyone in the first rule and then specifically allow access for users, groups, or computers in subsequent rules. This is because of the hierarchy of rules. That is, if you allow anyone access to a directory called /my_stuff, and then you have a subdirectory /my_stuff/personal that allows access to a few users, the access control on the subdirectory won't work because anyone allowed access to the /my_stuff directory will also be allowed access to the /my_stuff/personal directory. To prevent this, create a rule for the subdirectory that first denies access to anyone and then allows it for the few users who need access.
However, in some cases if you set the default ACL to deny access to everyone, then your other ACL rules don't need a "deny all" rule.
The following line denies access to everyone:
deny (all)
user = "anyone";
|
ACLs have a hierarchy that depends on the resource. For example, if the server receives a request for the document (URI) /my_stuff/web/presentation.html, the server first looks for an ACL that matches the file type or any other wildcard pattern that matches the request, then it looks for one on the directory, and finally it looks for an ACL on the URI. If there are multiple ACLs that match, the server uses the last statement that matches. However, if you use an absolute statement, then the server stops looking for other matches and uses the ACL containing the absolute statement. If you have two absolute statements for the same resource, the server uses the first one in the file and stops looking for other resources that match.
For example, using the ACL hierarchy with the request for the document /my_stuff/web/presentation.html, you could have an absolute ACL that restricts access to the file type *.html. Then the server would use that ACL instead of looking for one that matches the URI or the path.
version 3.01;
acl "default";
authenticate (user,group) {
prompt="Enterprise Server";
};
allow (read,execute,list,info)
user = "anyone";
allow (write,delete)
user = "all";
acl "*.html";
deny absolute (all)
user = "anyone";
acl "uri=/my_stuff/web/presentation.html";
deny (all)
user = "anyone";
allow (all)
user = "anyone";
|
Attribute qualifier expressions define who is allowed or denied access based on their user name, group name, host name, or IP address. The following lines are examples of allowing access to different people or computers:
ou can also restrict access to your server by time of day (based on the local time on the server) by using the timeofday attribute qualifier. For example, you can use the timeofday attribute qualifier to restrict access to certain users during specific hours.
Use 24-hour time to specify times (for example, use 0400 to specify 4 a.m. or 2230 for 10:30 p.m.). |
The following example restricts access to a group of users called guests between 8 a.m. and 4:59 pm.
allow (read)
(group="guests") and
(timeofday<800 or timeofday>=1700);
|
You can also restrict access by day of the week. Use the following three-letter abbreviations to specify days of the week: Sun, Mon, Tue, Wed, Thu, Fri, and Sat.
The following statement allows access for users in the premium group any day and any time. Users in the discount group get access all day on weekends and on weekdays anytime except 8am-4:59pm.
allow (read) (group="discount" and dayofweek="Sat,Sun") or (group="discount" and (dayofweek="mon,tue,wed,thu,fri" and (timeofday<0800 or timeofday>=1700))) or (group="premium"); |
You can use various operators in attribute qualifier expressions. You can use parentheses to delineate the order of precedence of the operators. With user, group, dns, and ip qualifiers, you can use the following operators:
With timeofday and dayofweek qualifiers, you can use the following additional operators:
After installing the server, the server uses the default settings in the file <server_root>/httpacl/generated.httpd-<serverid>.acl. There is also a file called genwork.httpd-<serverid>.acl that is a working copy the server uses until you save and apply your changes when working with the user interface. When editing the ACL file, you might want to work in the genwork file and then use the Server Manager to save and apply the changes.
The following text is from the default file:
# File automatically written
#
# You may edit this file by hand
#
version 3.01;
acl "default";
allow (read,execute,list,info)
user = "anyone";
allow (write,delete)
user = "all";
|
The default ACL file is referenced in magnus.conf as follows:
ACLFile <absolutepath>/generated.https-<serverid>.acl |
You can reference multiple ACL files in magnus.conf and then use their
ACLs for resources in obj.conf. However, the server uses only the first
ACL file with the web publisher and when evaluating access control for
objects that don't have specific ACLs listed in obj.conf. If you're
using the Server Manager forms to do some access control, the first ACL
file in magnus.conf should point to the file
generated.https-<serverid>.acl. See Referencing ACL files in
obj.conf for more information.
6.1.4 General syntax items
Input strings can contain the following characters:
If you use any other characters, you need to use double-quotation marks around the characters.
A single statement can be placed on its own line and terminated with a
semicolon. Multiple statements are placed within braces. A list of
items must be separated by commas and enclosed in double-quotation
marks (see the dayofweek example in "Attribute qualifier expressions"
on page 121).
6.2 Referencing ACL files in obj.conf
If you have named ACLs or separate ACL files, you can reference them in the obj.conf file. You do this in the PathCheck directive using the check-acl function. The line has the following syntax:
PathCheck fn="check-acl" acl="<aclname>" |
The aclname is a unique name of an ACL as it appears in any ACL file.
For example, you might add the following lines to your obj.conf file if you want to restrict access to a directory using the acl named sample_acl:
<Object ppath="/usr/ns-home/docs/test/*"> PathCheck fn="check-acl" acl="sample_acl" </Object> |
In the previous example, the first line is the object that states which server resource you want to restrict access to. The second line is the PathCheck directive that uses the check-acl function to bind the name ACL (sample_acl) to the object in which the directive appears. The sample_acl ACL can appear in any ACL file referenced in magnus.conf.
Netscape servers use an encryption system called Secure Sockets Layer (SSL) to ensure privacy when communicating with other SSL-enabled products, such as Netscape Navigator and Netscape Communicator.
For a complete discussion of encryption and SSL, see the online guide
Managing Netscape Servers.
7.1 What is encryption?
Encryption is the process of transforming information so it can't be decrypted or read by anyone except the intended recipient. This encrypted information is called ciphertext. It is the ciphertext that you send across the network. For example, suppose you have a financial report stored at your web site. If SSL is enabled on your server, your server encrypts the report and sends the ciphertext to a client, the client then decrypts the ciphertext back into the financial report.
Decryption reverses the process, turning the ciphertext back into the original message. Only the recipient can decrypt the text because only the recipient has the key. In fact, both the encryption and the decryption processes require keys.
Client-server communication with SSL uses two keys. The encryption key is called the public key, and the decryption key is the private key. SSL uses the two keys as follows:
There are other security risks besides someone trying to break your encryption. The modern network faces risks from external and internal hackers, using a variety of tactics to gain access to your server and the information on it.
So in addition to enabling SSL on your server, you should take extra security precautions. The following list describes the most important things you can do to make your server more secure. For more information on server security see the online guide Managing Netscape Servers.
You can prevent pre-encrypted files from being cached by a client by adding the following line inside the <HEAD> section of the file in HTML:
|
To enable SSL on your server, you must complete these steps:
Steps 1 through 3 must be done through the administration server. For more information about using the administration server to enable SSL, see Managing Netscape Servers. |
After you have generated a key-pair file and installed your certificate, activate SSL for your server by completing the following:
Most of the time, you want your server to run with SSL enabled. You might, at other times, want to disable it. If you temporarily disable SSL, make sure you re-enable it before processing transactions that require confidentiality, authentication, or data integrity. |
Now that SSL is enabled on your server, you can configure your overall
SSL preferences. See "Setting encryption preferences" on page 129 for
information on configuring encryption preferences for your server.
7.4 Setting encryption preferences
You can set system-wide preferences for SSL, including:
You can specify which versions of SSL your server can communicate with. The latest and most secure version is SSL version 3, but many older clients use only SSL version 2. You will probably want to enable your server to use both versions. To specify the SSL version:
You can configure the web server so that it refuses any client who doesn't have a client certificate from a trusted CA. This differs from access control in that all requests must be through SSL connections and they must be from clients who have certificates from trusted CAs. (See the online guide Managing Netscape Servers for details on configuring trusted CAs.)
With client certificates on, the server asks the client to send its certificate before the server will grant the request. The server doesn't care who the user is as long as that user has a valid certificate from a trusted CA. However, you can combine client certificates with access control so that in addition to being from a trusted CA, the user associated with the certificate must match the access-control rules. See Chapter 5 for more information.
To enable client authentication using trusted certificates:
If a user accessing the server doesn't have a certificate from a
trusted CA, the server returns an error stating, "The server cannot
verify your certificate." The server logs an error, but it doesn't list
the untrusted CA. If you want to know which CA issued the certificate
to the client, you need to use access control in addition to client
authentication. With access control and certificate mapping, the server
will log an error that lists the CA's distinguished name.
7.4.3 Selecting SSL ciphers
A cipher is an algorithm used in encryption. Some ciphers are more secure, or stronger, than others. Generally speaking, the more bits a cipher uses during encryption, the harder it is to decrypt the data. The list of available ciphers doesn't appear on the Encryption Preferences form unless you've enabled SSL. See Section 7.3 for more information. The Netscape FastTrack Server supports only 40-bit encryption. If you require stronger encryption than that provided by the Netscape FastTrack Server, contact Netscape for information about the Netscape Enterprise Server.
When initiating an SSL connection with a server, a client lets the server know what ciphers it prefers for encrypting information. In any two-way encryption process, both parties must use the same ciphers. Because a number of ciphers are available, your server needs to be able to use the most popular ones.
You can choose ciphers from the SSL 2 protocol, as well as from SSL 3. To specify which ciphers your server can use:
The SSL 2.0 ciphers include:
The SSL 3.0 ciphers include:
This section describes what effects you need to know about while
running an SSL-enabled server.
7.5.1 Secure URL construction
URLs to an SSL-enabled server are constructed using https instead of simply http. URLs that point to documents on an SSL-enabled server have this format:
https://servername.domain.dom/pathname/unique_file_identifier |
After SSL is installed and enabled on a server, all communications between the server and SSL-enabled browsers (such as Netscape Communicator) are private, authenticated, and checked for message integrity. Thus, any document sent to a user with an SSL-enabled browser is automatically encrypted.
Browsers not enabled with SSL can't communicate with an SSL-enabled server because they can't initiate an SSL transaction. However, they can communicate with the server when the server isn't using SSL. |
Once SSL is enabled, a new log file, (secure.log) is created in the normal log directory. Entries in the log look like this:
198.93.92.99: [02/Nov/1994:23:51:46 -0800] using keysize 40 |
The IP address is first, followed by the date and time of access, and then the key size. The key size represents a level of security. Generally, the bigger the key size, the higher the level of security. See Section 7.4.3 for a list of supported key sizes.
Your server still uses the access.log file to log information about
server accesses; however, all information regarding secure transactions
is logged in secure.log.
7.5.4 Unprotected server document directory
If you want to have both protected and unprotected servers, you should operate the unprotected server on a different machine from the protected one. If your resources are limited and you must run an unprotected server on the same machine as your protected server, do the following:
Installing an SSL-enabled server creates new directive entries in the
magnus.conf file (the server's main configuration file). These new
directives are briefly described in the following sections.
7.5.5.1 Security
The Security directive tells the server whether SSL is enabled or disabled.
Syntax
Security value |
value specifies if SSL is on or off. Set the value parameter to on to
enable SSL; and to off to disable SSL.
7.5.5.2 SSL2
The SSL2 directive tells the server whether SSL2 is enabled or disabled.
Syntax
SSL2 value |
value specifies whether SSL version 2 is enabled or disabled. Set the
value parameter to on to enable SSL 2 and to off to disable SSL 2.
7.5.5.3 SSL3
The SSL3 directive tells the server whether SSL3 is enabled or disabled.
Syntax
SSL3 value |
value specifies whether SSL version 3 is enabled or disabled. Set the
value parameter to on to enable SSL 3, and to off to disable SSL 3.
7.5.5.4 KeyFile
The KeyFile directive tells the server where the key file is located.
Syntax
KeyFile keyfile |
keyfile is the server's key file, specified as an absolute path from
the server root.
7.5.5.5 CertFile
The CertFile directive specifies where the certificate file is located.
Syntax
CertFile certfile |
certfile is the server's certificate file, specified as an absolute
path from the server root.
7.5.5.6 Ciphers
The Ciphers directive specifies the ciphers enabled for your server. For a discussion of these ciphers, refer to Section 7.4.
Syntax
Ciphers +rc4 +rc4export -rc2 -rc2export +idea +des +desede3 |
A + means the cipher is active, and a - means the cipher is inactive.
Any cipher with export as part of its name is not stronger than
7.5.5.7 SSL3Ciphers
The SSL3Ciphers directive specifies which SSL 3 ciphers are enabled for your server. For a discussion of these ciphers, refer to Section 7.4.
Syntax
SSL3Ciphers +rsa_rc4_128_md5 +rsa_3des_sha +rsa_des_sha +rsa_rc4_40_md5 +rsa_rc2_40_md5 -rsa_null_md5 |
A + means the cipher is active, and a - means the cipher is inactive.
Any cipher with 40 as part of its name is 40 bits.
7.5.5.8 SSLClientAuth
The SSLClientAuth directive specifies whether a client must have a certificate in order to communicate with the server. You don't need to turn on this directive to use client authentication with access control.
Syntax
SSLClientAuth value |
value specifies if certificates are always required. Set the value parameter to on to require certificates, and to off to specify that certificates are not required.
In addition to serving HTML documents, your server can run programs that interact with clients. These applications that run on the server computer are called server-side applications. (Client-side applications, which are downloaded to the client, run on the client machine.)
Your server can run these types of server-side applications:
This chapter describes how to install Java applets, CGI programs, and JavaScript applications onto your server. Plug-ins extend or replace your server's features. For example, you can use plug-ins to provide a different way to control access, or different logging mechanisms.
For information on writing and installing plug-ins, see the DevEdge site at:
http://developer.netscape.com/library/documentation/ |
Additionally, your server can send these types of client-side applications to clients:
This chapter deals mainly with the installation and configuration of server-side programs, although you'll find some information on client-side applications as well.
Additionally, this chapter describes the steps for specifying a default
query handler CGI program. (A query handler processes text sent to it
via the ISINDEX tag in an HTML file.)
8.1 Installing server-side programs
Java applets, JavaScript applications, and CGI programs have different strengths and uses. Java is a full-featured programming language for creating network applications. CGI (Common Gateway Interface) programs can be written in C, Perl, or other programming languages; what makes them all CGI programs is the standard way they pass information between clients and servers. JavaScript applications are written in JavaScript, an object-based scripting language; it is easier to learn than an object-oriented programing language and lends itself to rapid application development.
Each type of program is installed onto the server differently. The following list summarizes the procedures:
These installation procedures are described in the following sections.
8.1.1 Installing server-side Java applets
Java is a programming language designed for platform-independent application development. If you have a server-side Java applet that works on a Unix server, you can also use it with a server running on Windows NT. Like a CGI program, a server-side Java applet is triggered by a client sending or requesting information in the form of a URL. However, server-side Java applets and client-side Java applets have different formats and are not interchangeable.
To use server-side Java applets with your server, you must enable your server's Java interpreter and copy all Java applets into a specified directory. All server-side Java applet files must be named in the standard format name.class. For more information on creating Java applets that work with your server, refer to Netscape's DevEdge online documentation web site at:
http://developer.netscape.com/library/documentation/ |
To enable your server to use server-side Java applets:
Be sure to copy all server-side Java applets into the directory you
specified.
8.1.2 Installing CGI programs
Common Gateway Interface, or CGI, programs can be created with any number of programming languages. On a Unix machine, you're likely to find CGI programs written as Bourne shell or Perl scripts. On a Windows computer, you might find CGI programs written in C++ or batch files.
Regardless of the programming language, all CGI programs accept and return data in the same manner, as described in Netscape's DevEdge online documentation web site at:
http://developer.netscape.com/library/documentation/ |
There are two ways to store CGI programs on your server machine:
There are benefits to either implementation. If you want only a specific set of users to be able to add CGI programs, keep the CGI programs in specified directories and restrict access to those directories. If you want to allow anyone who can add HTML files to be able to add CGI programs, use the file type alternative. Users can keep their CGI files in the same directories as their HTML files.
If you choose the directory option, your server will attempt to
interpret any file you place in that directory as a CGI program. By the
same token, if you choose the file type option, your server will
attempt to process any files with the file extensions .cgi, .exe, or
.bat as CGI programs. If a file has one of these extensions but is not
a CGI program, an error occurs when a user attempts to access it.
8.1.2.1 Specifying a CGI-only directory
To specify a CGI-only directory:
http://yourserver.domain.com/cgi-bin/program-name |
The URL prefix you specify can be different from the real CGI directory you specify in the next step. |
To remove an existing CGI directory, click that directory's Remove button in the CGI Directory form. To change the URL prefix or CGI directory of an existing directory, click that directory's Edit button.
Copy your CGI programs into the directories you've specified.
Remember--any file in those directories will be processed as a CGI
file, so you don't want to put HTML files in your CGI directory.
8.1.2.2 Specifying CGI as a file type
To specify CGI programs as a file type:
The CGI files must have the file extensions .bat, .exe, or .cgi. Any
non-CGI files with those extensions will be processed by your server as
CGI files, causing errors.
8.1.2.3 Downloading executable files
If you're using .exe as a CGI file type, users will not be able to download .exe files as executables.
One solution to this problem is to compress the executable files that you want users to be able to download, so that the extension is not .exe. This solution has the added benefit of making the download time shorter.
Another possible solution is to remove .exe as a file extension from the magnus-internal/cgi type and add it instead to the application/octet-stream type (the MIME type for normal downloadable files). However, after making this change you cannot use .exe files as CGI programs.
To do this, complete the following:
Another solution is to edit your server's obj.conf file to set up a download directory, where any file in the directory is downloaded automatically. The rest of the server won't be affected. For directions on setting up this directory, see the technical note at:
http://help.netscape.com/kb/server/960513-130.html |
You can specify a default query handler CGI program. A query handler processes text sent to it via the ISINDEX tag in an HTML file.
ISINDEX is similar to a form text field in that it creates a text field in the HTML page that can accept typed input. Unlike the information in a form text field, however, the information in the ISINDEX box is immediately submitted when the user presses Return. When you specify your default query handler, you tell your server to which program to direct the input. For an in-depth discussion of the ISINDEX tag, see an HTML reference manual.
To set a query handler, do the following:
Web Application Interface (WAI) services are a kind of plug-in that use the Common Object Request Broker Architecture (CORBA).
Before you use WAI services, you must enable them on your server. Enabling WAI services essentially turns on Internet Inter-ORB Protocol (IIOP) support on the server. You may have other (non-WAI) applications that need this support. If you need IIOP support, enable WAI services.
To enable WAI services on your server:
For more information about WAI, see Writing Web Applications with WAI on Netscape's DevEdge online documentation web site at:
http://developer.netscape.com/library/documentation/ |
To install server-side JavaScript programs, you need to activate server-side JavaScript for your server and use the Application Manager. This section includes information on accessing and using the Application Manager to install server-side JavaScript applications, as well as perform other functions.
For more information about writing JavaScript applications, see Writing Server-Side JavaScript Applications on Netscape's DevEdge online documentation web site at:
http://developer.netscape.com/library/documentation/. |
If you are using server-side JavaScript applications, you must first activate server-side JavaScript for your server.
To enable server-side JavaScript:
For applications written in server-side JavaScript, you can perform many administrative tasks with the server-side JavaScript Application Manager. Using the Application Manager, you can do the following:
To run the Application Manager:
You can also run the Application Manager by activating server- side JavaScript and then loading the following URL in Communicator:
http://server.domain/appmgr |
You see the screen in Figure 8-1.
Figure 8-1 Application Manager
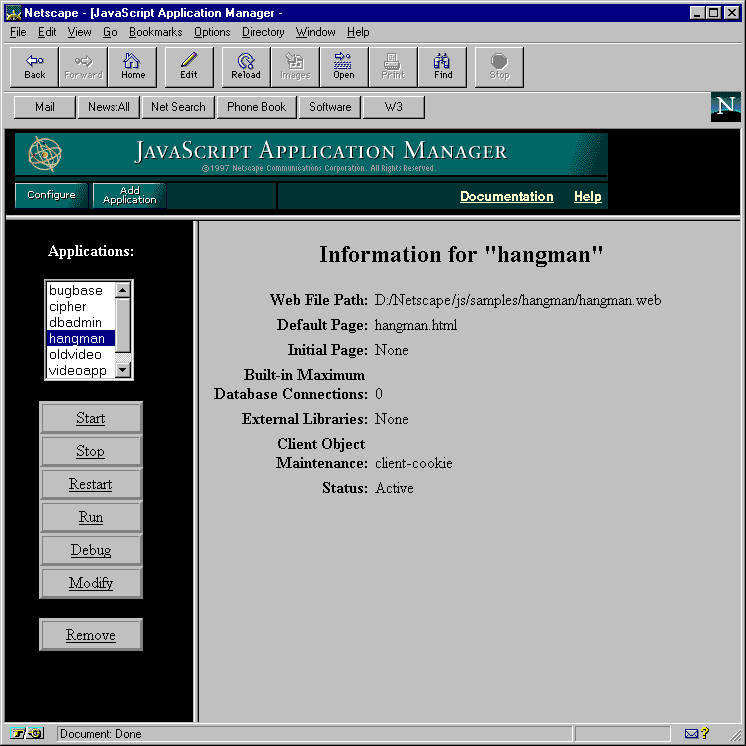
The Application Manager displays all applications currently installed on the server in a scrolling list in the left frame. Select an application by clicking its name in the scrolling list.
For the selected application, the right frame displays:
Click the task buttons in the left frame to perform the indicated action on the selected application. For example, to modify the installation parameters of the selected application, click Modify.
Click Configure to configure the default settings for Application
Manager. Click Add Application to add/install a new JavaScript
application. Click Documentation for further documentation on
server-side JavaScript. Click Help for instructions on using the
Application Manager.
8.1.5.3 Securing the Application Manager
Your Application Manager runs on your web server (rather than on the administration server). The Application Manager is installed into the js/ appmgr directory. You can access it without the Server Manager with this URL:
|
Consequently, you may want to restrict access to the Application Manager URL and the application URI so that only you and any other trusted administrators can access them. If you don't restrict access to the Application Manager, anyone can add, remove, modify, start, and stop applications on your server.
If you want to require the administration server user name and password for access to the Application Manager, follow these steps:
You then must enter the administration server user name and password to use the Application Manager.
If your server does not use the Secure Sockets Layer (SSL), the user
name and password for the Application Manager are transmitted
unencrypted over the network. Any intruder who intercepts this data may
be able to access the Application Manager. If you use the same password
for your administration server, the intruder can also control your
server. For security reasons, do not use the Application Manager from
outside of your firewall unless you are using SSL.
8.1.5.4 Installing server-side JavaScript applications
You can install up to 120 JavaScript applications on one server.
You must install (add) an application with the Application Manager before you can run it. To install a new application:
Don't give any JavaScript applications the same names as any subdirectories of your primary document directory. If you do, the server will no longer correctly process requests from the directory. For example, if you have a directory server_root/docs/bug, and a JavaScript application named bug, all requests for any files in the bug directory (or any of its subdirectories) will attempt to launch the JavaScript application bug. The JavaScript application URI takes precedence. |
When you install a server-side JavaScript application, you must enter a name for it. This name determines the application URL, the URL that clients use to access a JavaScript application. Application URLs are of the form:
http://server.domain/appName/page.html |
where server is the name of the HTTP server, domain is the Internet domain (including any subdomains), appName is the application name you enter when you install it, and page is the name of a page in the application.
For example, if your server is named myserver and your domain name is mozilla.com, the application URL for the Hello World sample application is http://myserver.mozilla.com/world/hello.html.
When a client requests this URL, the server generates HTML for the specified page in the application and sends it to the client.
Before you install an application, make sure the application name you choose does not usurp an existing URL on your server. All client requests for URLs that match the application URL are routed to the directory specified for the .web file, circumventing the server's normal document root. |
Using the previous example, any requests for URLs that begin with
http://myserver.mozilla.com/world will look for documents in the
js/samples/world directory and not in your server's normal document
root.
8.1.5.6 Controlling access to a server-side JavaScript application
When you install an application, you may want to restrict its use to
only certain users. You can do this by applying a configuration style
to the application.
8.1.5.7 Modifying installation parameters
To modify an application's installation parameters:
You can change any of the parameters defined when you installed the application, except the application name. To change the name of an application, you must remove the application and then reinstall it.
If you modify the parameters of a stopped application, the Application
Manager automatically starts it. When you modify parameters of an
active application, Application Manager automatically stops and
restarts it.
8.1.5.8 Removing a server-side JavaScript application
To remove an installed application:
If you delete an application, and you subsequently want to run it, you
must install it again.
8.1.5.9 Starting, stopping, and restarting a server-side JavaScript application
To start, stop, or restart an installed application:
You can also start, stop, and restart an application by entering a special URL of the form:
http://server.domain/appmgr/control.html?name=appName&cmd=action |
where appName is the application name and action is either stop, start,
or restart.
8.1.5.10 Running a server-side JavaScript application
There are two ways to run an installed application:
If you attempt to run a stopped application (one that is not active),
then the Application Manager tries to start it first.
8.1.5.11 Configuring default settings
To configure default parameter settings for the Application Manager:
When you install a new application, the default installation parameters are used for the initial settings.
You can specify the following default settings:
Installing client-side programs in your server is relatively easy.
There are two types of client-side programs: Java applets and
JavaScript programs. Client-side Java applets are executable files
identified in an HTML document, retrieved from the server, and executed
on the client. The applets can reside anywhere under your server's
primary document root. Client-side JavaScript programs are embedded in
HTML files and executed on the client.
8.2.1 Installing client-side Java applets
Instructions for creating client-side Java applets are outside the
scope of this book. After you've created an applet, to install it you
must copy it into a directory from which your server can deliver it. To
send it to a client, it must be referenced in an HTML file.
8.2.2 Installing client-side JavaScript programs
Client-side JavaScript programs are created by lines of JavaScript code embedded in HTML files. The HTML files travel from the server to the client. Once the files reach the client, Communicator interprets the JavaScript code and performs the specified actions.
With LiveConnect you can connect server-side Java and JavaScript applications, or client-side Java and JavaScript applications. For more information on LiveConnect, on embedding JavaScript in HTML, and on using client-side JavaScript with other programs, refer to the documentation on the DevEdge online documentation web site at:
http://developer.netscape.com/library/documentation/ |
You can monitor your server's activity using several different methods.
You can view the server's status in real time by using the Hypertext
Transfer Protocol (HTTP). You can also monitor your server by recording
and viewing log files.
9.1 Working with log files
Server log files record your server's activity. You can use these logs
to monitor your server and to help you when troubleshooting. The error
log file, located in httpd-servername/logs in the server root
directory, lists all the errors the server has encountered. The access
log, located in httpd-servername/logs in the server root directory,
records information about requests to the server and the responses from
the server. You can use the Server Manager to specify what to include
in the access log file. Use the log analyzer to generate server
statistics. You can back up server error and access log files by
archiving them.
9.1.1 Viewing an access log file
You can view the server's active and archived access log files from the Server Manager.
To view an access log:
Here is an example of an access log in the Common Logfile Format:
wiley.a.com - - [16/Feb/1996:21:18:26 -0800] "GET / HTTP/1.0" 200 751 wiley.a.com - - [17/Feb/1996:1:04:38 -0800] "GET /docs/grafx/icon.gif HTTP/1.0" 204 342 wiley.a.com - - [20/Feb/1996:4:36:53 -0800] "GET /help HTTP/1.0" 401 571 arrow.a.com - john [29/Mar/1996:4:36:53 -0800] "GET /help HTTP/1.0" 401 571 |
Table 9-1 describes the last line of the sample access log.
| Access Log Field | Example |
|---|---|
| Hostname or IP address of client | arrow.a.com. (In this case, the hostname is shown because the web server's setting for DNS lookups is enabled; if DNS lookups were disabled, the client's IP address would appear. ) |
| RFC 931 information | (RFC 931 identity not implemented) |
| User name | john (user name entered by the client for authentication) |
| Date/time of request | 29/Mar/1996:4:36:53 -0800 |
| Request | GET /help |
| Protocol | HTTP/1.0 |
| Status code | 401 |
| Bytes transferred | 571 |
Here is an example of an access log using the flexible logging format:
wiley.a.com - - [25/Mar/1996:12:55:26 -0800] "GET /index.htm HTTP/1.0" "GET" "/?-" "HTTP/ 1.0" 304 0 - Mozilla/2.0 (WinNT; I) wiley.a.com - - [25/Mar/1996:12:55:26 -0800] "GET / HTTP/1.0" "GET" "/?-" "HTTP/1.0" 304 0 - Mozilla/2.0 (WinNT; I) wiley.a.com - - [25/Mar/1996:12:55:26 -0800] "GET / HTTP/1.0" "GET" "/?-" "HTTP/1.0" 304 0 - Mozilla/2.0 (X11; I; IRIX 5.3 IP22) |
The access log in the flexible logging format looks similar to the
access log using the Common Logfile Format.
9.1.2 Viewing the error log file
The error log file contains errors the server has encountered since the log file was created; it also contains informational messages about the server, such as when the server was started. Incorrect user authentication is also recorded in the error log. Use the error log to find broken URL paths or missing files.
To view the error log file:
Here is an example of an error log:
[13/Feb/1996:16:56:51] info: successful server startup
[20/Mar/1996 19:08:52] warning: for host wiley.a.com trying to
GET /report.html,
append-trailer reports: error opening /usr/ns-
home/docs/report.html (No such file or
directory)
[30/Mar/1996 15:05:43] security: for host arrow.a.com trying to
GET /, basic-ncsa
reports: user jane password did not match database /usr/ns-
home/authdb/mktgdb
|
In this example, the first line is an informational message--the server
started up successfully. The second log entry shows that the client
wiley.a.com requested the file report.html, but the file wasn't in the
primary document directory on the server. The third log entry shows
that the password entered for the user jane was incorrect.
9.1.3 Setting log preferences
During installation, an access log file named access was created for the server. You can customize access logging for any resource by specifying whether to log accesses, what format to use for logging, and whether the server should spend time looking up the domain names of clients when they access a resource.
Server access logs can be in Common Logfile Format, flexible log format, or your own customizable format. The Common Logfile Format is a commonly supported format that provides a fixed amount of information about the server. The flexible log format allows you to choose (from the Server Manager) what to log. A customizable format uses parameter blocks that you specify to control what gets logged. Once an access log for a resource has been created, you can't change its format unless you archive it or create a new access log file for the resource.
To set access logging preferences:
http://developer.netscape.com/library/documentation/ |
You can archive the access and error log files and have the server create new ones.
When you archive log files, the server renames the current log files and then creates new log files with the original names. You can back up or archive (or delete) the old log files, which are saved as the original filename followed by the date and time the file was rotated. For example, access might become access.24Apr-04AM.
You can archive log files immediately or have the server archive log files at a specific time on specific days. The information about when to archive log files is stored in the cron.conf file in the admin-serv directory in the server root directory; the server's cron configuration options are stored in ns-cron.conf in the admin-serv directory.
Before running the log analyzer, you should archive the server logs. |
To archive log files:
You can monitor your server's usage with the interactive server monitor. You can see how many requests your server is handling and how it is handling these requests. If the interactive server monitor reports that the server is handling a great number of requests, you may need to adjust the server configuration or the system's network kernel to accommodate the requests.
To monitor your server:
The interactive server monitor reports the totals for the following server values:
Use the log analyzer to generate statistics about your server, such as a summary of activity, most commonly accessed URLs, times during the day when the server is accessed most frequently, and so on. You can run the log analyzer from the Server Manager or the command line.
Before running the log analyzer, you should archive the server logs. See Section 9.1.4 for more information. |
To run the log analyzer from the Server Manager:
| Previous | Next | Contents |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
| privacy and legal statement | ||
| 6563PRO_002.HTML | ||